Conference: Cyber Security Summit (Charlotte) 2019
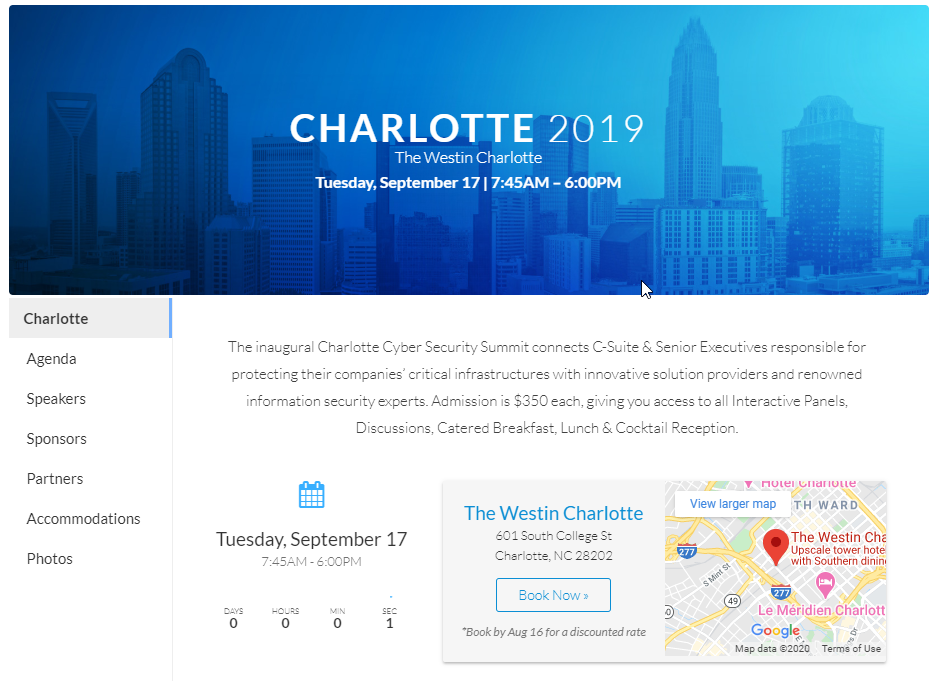
This month I had the pleasure of attending the Cyber Security Summit in Charlotte at in The Westin on September 17, 2019.
The summit was a single day connecting "C-Suites & Senior Executives responsible for protecting their companies' critical infractructures with innovative solution providers and renowned information security providers" (from the site). The conference was sponsored by ExtraHop, a cloud network security company.
For those that have never been to one of these, I find the single day and single track format fairly good. The conference focus on C-Suite and Senior executives led to many of the talks throughout the day just outside the realm of technical which worked well for these type of conference; the same focus was also seen within the vendor hall.

ExtraHop's John Smith gave the keynote and the first talk of the day which centered around the problems the volumes and diversification of our data. From 2005 to 2025 (theorized), we would have increased the amount of data stored by 43%. The level of volume of stored day causes concern for SOCs trying to perform incident response and threat hunting. They hit on a big topic all day: machine learning. They give information on how to prove SOcs today by adding machine learning to improve human analysis. Machines crunch numbers and large amounts of data but finding anomalies can be difficult, and at least for now, requires human touch.

Next, DarkTrace's Marcus Fowler talk about the evolving threats through the use of machine learning and artificial intelligence. Threats today continue to increase in speed and sophistication while the access to advance tools are common place for many entry level cyber criminals. DarkTrack went on to talk about their platforms: The Enterprise Immune System and Antigena. These platforms are named after the human immune system and antigens. For the immune system, it was explained the system learns in real-time with no prior bias. It learns what is 'normal' and detects threats on the fly while surfacing high priority threats to teams. When using it with the Antigena, enterprises can get autonomous responses. This means the system can change security rules on the fly or repeat and action depending on pre-configured rules, learning configuration, or response from an analyst. There is also a mobile application that could be used to take action on security risks in a network from activating a security change or calling a incident response team.

IBM Security's David Cass spoke about moving and security information in the cloud. One of the biggest things mentioned was adapting the cloud based on business value due to workload not to save money. He listed several key concerns:
- protected from latest threats
- critical data protected
- adapting to the platform
- requiring specific skill-sets
- maximizing security value
- transparency with leadership
He also spoke about the difference of data sovereignty vs data residency (not the same thing). Then continued to talk about business continuity and disaster recovery for cloud environments and stressing proper testing and planning. He makes a point about understanding the journey to the cloud and the proper way to plan and deploy applications to the systems.

@RISK Technologies's Sean O'Brien gave a talk on Identity & Management (IAM) and Governance centering around their IDMWORKS platform. They deep dived into a 5 level diagram through how to get to a mature IAM model. After understanding the model, they moved to how to assess the IAM system for two reasons (from the slides):
- to determine the capabilities needed to ensure the right people get access to the right resources at the right times for the right reasons (the why)
- practical, structured and coherent approach to the management of users' identities and their access to systems and data (the what)
He then goes into a talk about how to maintain the IAM program through governance and ensuring the whole organization is directly involved in the process.
There were three different panels as well which were a bit harder to follow for notes in this format (also some technical problems with mics). There were a wide range of questions and answers as well. I should have taken some better notes during these sections.
The vendor hall had numerous vendors; I thought it was alright but it was a bit repetitive. Most of the technology companies there had demos setup centered around dashboards and information systems where notifications showed up and to be acted on. I figured it must be the age of dashboards. There was also training and certification companies and other random things. A list is located on the website under sponsors and partners. Also, for those with training requirements, there was a 6 CEUs given out as well if you remained throughout the day.