Forensics on Cisco Collaboration
Note: originally submitted for requirement in DFS-575 at Champlain College Online for MS in Digital Forensics. This work as been reformatted and changed from the original submission.
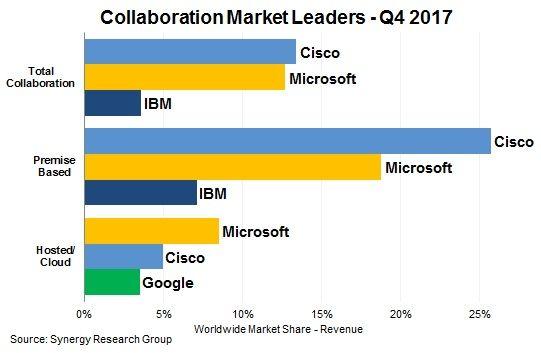
Cisco Collaboration controls more market share then Microsoft, IBM, and Google for total collaboration and on premise solutions [1].
Cisco Systems, Inc was found in 1984 by Leonard Bosack and Sandra Lerner. They
derived the name from San Francisco where the company was originally created and written as “cisco Systems”; some time later, Stanford, where both Bosack and Lerner worked, licensed their proprietary software to the company. Cisco’s first break came in 1985 from selling a router supporting multiple network protocols [2].
Cisco grew their business largely in the 1990s with the help of it’s CEO John T.
Chambers. Chambers initially set goals at Cisco to create a conversed network—carrying network, voice, and data over a single connection [3]. Voice-over-IP technology did enter Cisco’s portfolio until the purchase of Selsius Systems in 1998. Cisco further expanded their collaboration systems with the purchase of TelePresence in 2006 giving them extended videoconferencing technology [2].
Objective
Examining of Cisco Collaboration systems centered around its Cisco Jabber. Cisco purchased Jabber, Inc. in 2008 to “enhance the existing presence and messaging functions of Cisco’s Collaboration portfolio”. According to Cisco, “Jabber provides a carrier- grade, best-in-class presence and messaging platform. Jabber's technology leverages open standards to provide a highly scalable architecture that supports the aggregation of presence information across different devices, users and applications” and “enables collaboration across different presence systems” [4].
Cisco Jabber Features
Cisco Jabber 12.5 was release in 2019 providing the premiere collaboration tool from Cisco Systems, Inc. merging instant messaging, voice, video, desktop sharing, conferencing, and presence. Although this paper exams only the client on Windows, the client is also available for Android, iPhone/iPad, and Mac with complete integration of services between devices.
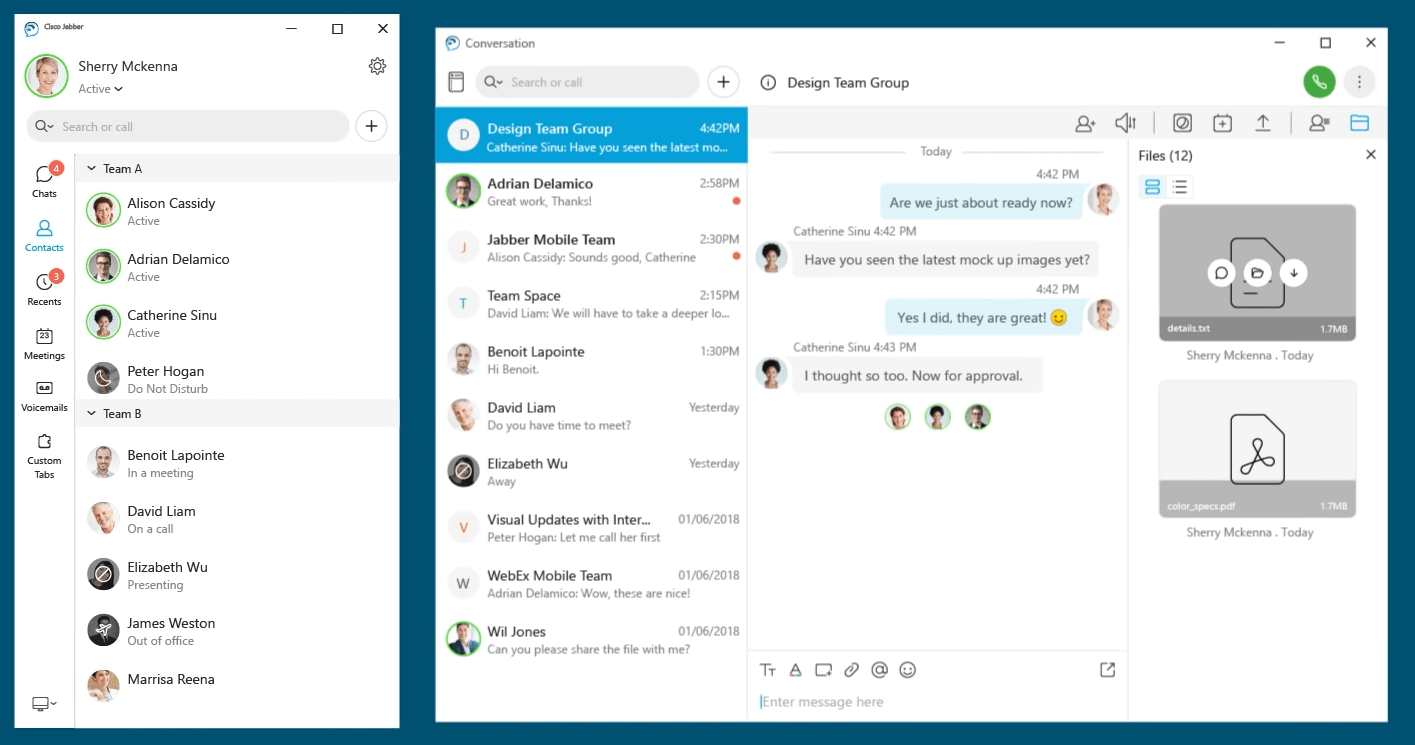
Figure below shows the interface of Cisco Jabber 12.5. The image shows the main chat window on the left with the logged in user at the top and each of the different sections for Chats, Contacts, Recents, Meetings, Voicemails, and Custom Tabs [5]. The left side of the image shows the conversions between individual users and team messages (group chats). The modern interface is similar to other collaboration application such Slack, Discord, or Skype providing an easy to use tool.
Software/Hardware Requirements
Cisco Jabber requires both CUCM and IM&P for the complete collaboration environment. Cisco does provide some limited software capabilities between different servers; to limit problems between versions, the lab centers around version 12.5 software versions of CUCM, IM&P, and Jabber Client. The following table shows the supported version (partial list) for features required for this lab [6]:
| Service | Software Requirement | Support Version |
|---|---|---|
| IM and Presence | Cisco Unified Communications Manager IM and Presence Service | 10.5(2) and later (minimum) 11.5(1) SU2 or later (Recommended) |
| Telephony | Cisco Unified Communications Manager | 10.5(2) and later (minimum) 11.5(1) SU3 or later (Recommended) |
| Contact Search | LDAP directory | LDAP v3 complaint directory such as Microsoft Active directory 2008 R2 and Open LDAP 2.4 or later |
Cisco Jabber requires the use of domain server system (DNS) and Windows version 7 or higher but does not require Microsoft .NET Framework or Java Modules [6].
Lab Architecture
The figure below shows the architecture of the lab used for examining the Cisco Jabber client. For an in-depth look at how it was configured see the Lab Configuration guide post.
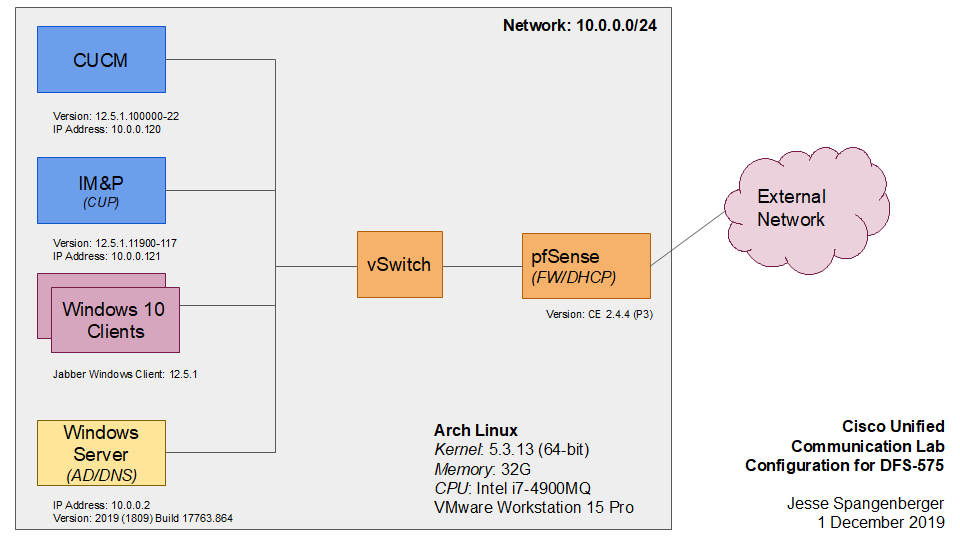
CUCM provides PBX capabilities (call routing, call control, class of service, etc.) for enterprise telephony. IM&P provides the instance messaging and presence for the system. Windows Server 2019 provides centralized user database and security of the Windows enterprise network—security of the systems is not covered in this paper. Two Window 10 Professional clients represent two users who are communicating between each other. Two parts of collaboration not shown above are voicemail and videoconferencing. Cisco Unity provides voicemail and auto-attendant, while Cisco Webex provides the videoconferencing.
Forensic Acquisition
KAPE and FTK Imager (with forensic suite) were used to gather the data from the Windows clients. Only the Windows clients were examined for this review of the Cisco Jabber client due to the complex, undocumented nature of the Windows servers. However, some of the information from the server can be captured.
Kroll Artifact Parser and Extractor (KAPE)
History. KAPE is another tool created by Eric Zimmerman, former FBI agent and certified SANS instructor. Per Zimmerman [7], “KAPE is primarily a triage program [that targets] a device or storage location, find the most forensically relevant artifacts, and parses them within a few minutes.” It provides those functions by collection files then processing the file sets through modules. Files are gathers through a configurations called targets while they are processed through modules, which are configuration files which run third party tools. These third party tools need to be downloaded and placed within KAPE’s folder [7]. The tool does store information in a temporary folder; after it collects all the artifacts, it will create a virtual hard drive v2 (VHDX) file which is zipped and transferred with the logs to the STFP server.
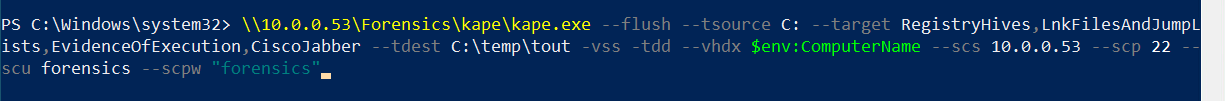
Collection Methodology. KAPE maybe run on the local box or remotely through UNC paths. Mark Hallman’s SANS webcast named “Enabling KAPE at Scale” shows how to run KAPE in these remote scenarios [8]. First, a windows share was setup on a Windows 10 forensic box and shared as read-only to the Windows 10 Clients. Next, KAPE’s runtime folder was put at the root of the shared drive. This provides the clients to run the script through a UNC path. Lastly, KAPE was executed with the ‘--sftpc’ command on the Windows 10 forensic box to startup an SFTP server that the clients cannot upload to. Figure 3 shows the command executed on the client workstation. The command collects the artifacts of Registry Hives, Link Files and Jump Lists, Evidence of Execution, and Cisco Jabber user’s chat history and then, it uploads it to the SFTP server 10.0.0.53 using the default port number and an username/password combination. The program uploaded an VHDX to the SFTP server.
Autopsy and FTK Imager with Virtual Machine Disk (VMDK)
History—Autopsy. Autopsy (v. 4.13.0) was originally a front-end to The Coroner’s Toolkit (TCT) and TCTUTILS in 2001. Basis Technology rewrote Autopsy v3 over top The Sleuth Kit (TSK) making a completely open-source and extendable platform for digital forensics software suite.
History—FTK Imager. FTK Imager (v 4.3.0.2) is a free application created by AccessData, founded in 1987, as 6 global offices, and created the Forensic Toolkit (FTK) [9]. FTK Imager’s primary function is as a “data preview and imaging tool” providing a tool to create images to be analyzed by forensics tools or suite [10]. This tool is one of the primary ways to forensically image a wide range of physical and virtual drives.
History—Virtual Machine Disk (VMDK). VMware created the virtual machine disks “to mimic operation of physical disk” and nearly all VMware products (Workstation, Fusion, ESX, and ESXi) support the VMDK format with slight differences. The current version, VMDK 5.0, was introduced with Workstation 5 [11]. Virtual machines created in VMware products provide snapshot support. Snapshots freeze a virtual machine at moment in time allowing the state of the machine (memory state, disk data, and power state) to be saved, restored, or cloned freely by an administrator. The snapshots works through a series of disk changes (similar to a complex Unix file diff) to keep track and boot each machine [11]. VMware’s article "Overview of virtual machine snapshots in vSphere", VMware KB 1015180, goes into details on how snapshots work.
Collection Methodology. Virtual machines created in VMware Workstation, or other products, are stored within a single directory with a series of files as shown in figure below. In this figure, Windows-10-UCS-2.vmdk is the main drive file; however, it contains only the base drive image.
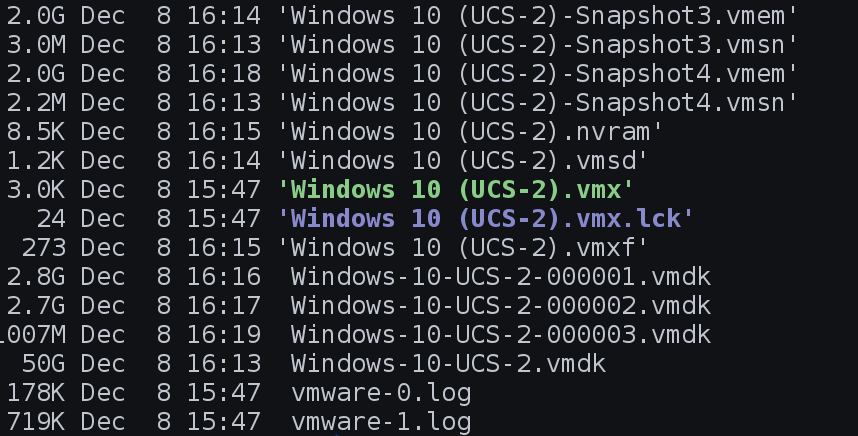
Windows-10-UCS-10-000003.vmdk contains the latest snapshot and information for the drive. This is the file to open in FTK Imager by File > Create Disk Image ... and choosing Image File, and then **Browse...", Figure 7 shows the Create Image dialog box after you choose the image source.
Windows-10-UCS-10-000003.vmdk is the file chosen as the image source and “E01” is the output file container. This creates a single file with the base image and the snapshots combined. This new file can be imported into any tool required.
Forensic Findings
Local Chat History
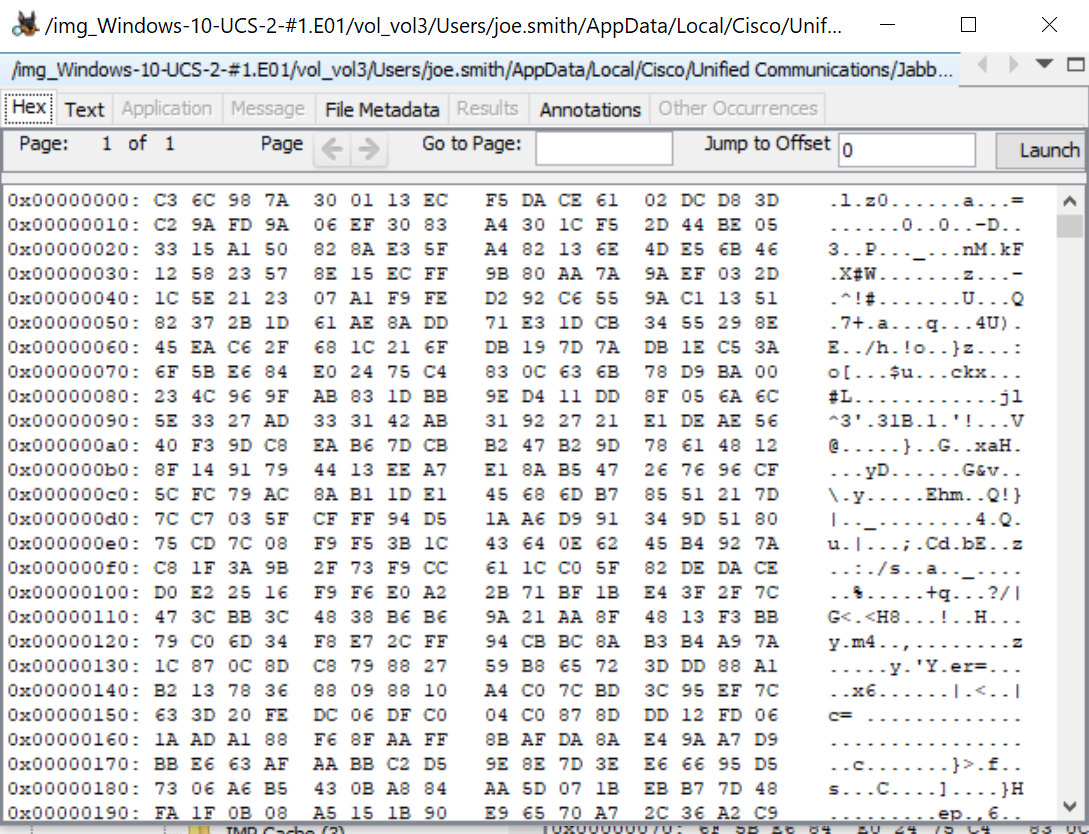
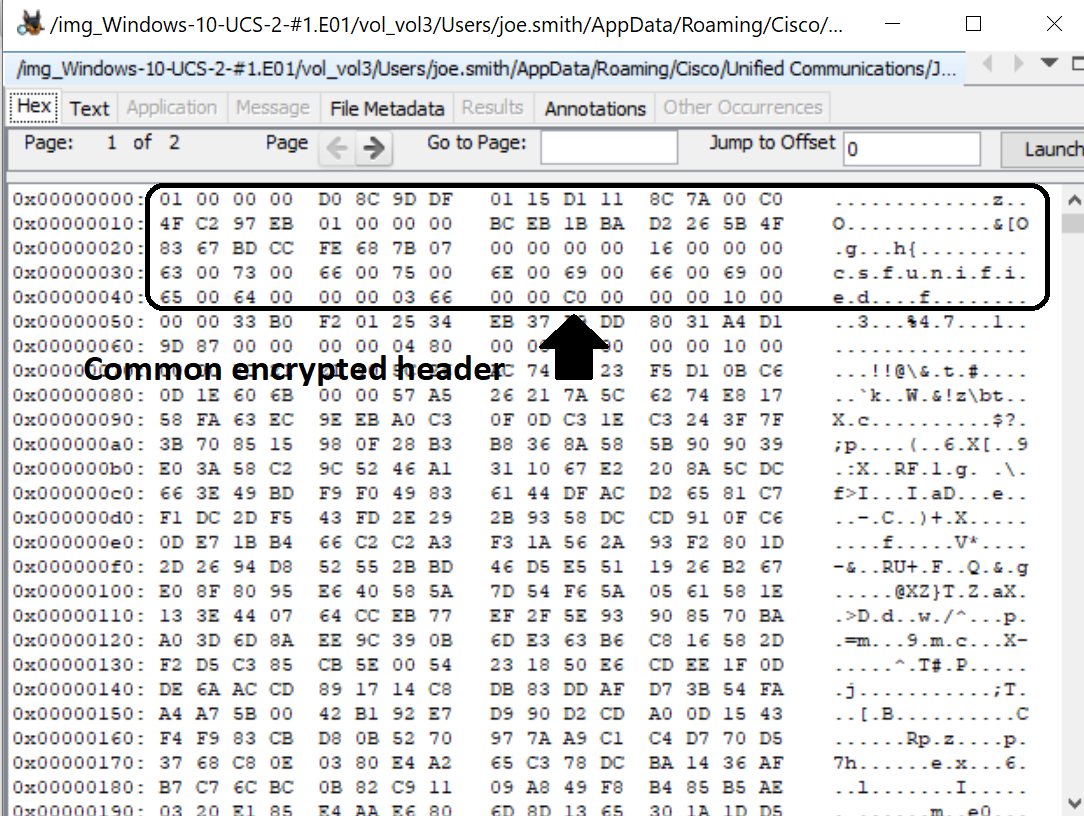
KAPE’s target CiscoJabber returns only the client history file located at %USERPROFILE%\AppData\Local\Cisco\Unified Communications\Jabber\CSF\History\uri@domain where uri equals username@domain. Per Planning Guide for Cisco Jabber 12.5, “Cisco Jabber does not encrypt archived instant messages when local chat history is enabled” and is a SQLite database [6]. However, the figure to the left shows that the file is encrypted and not view-able.
Setting Files
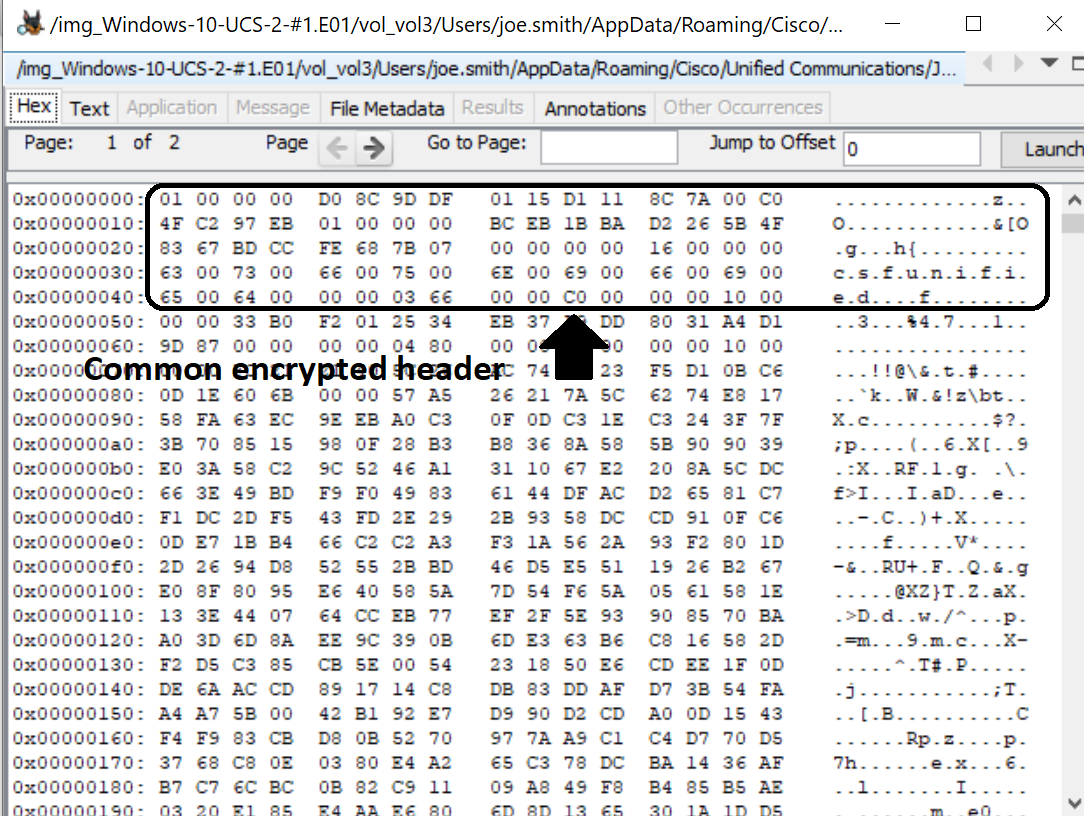
In addition to the chat history, nearly all settings files are encrypted with “csfunified” in the 60 bytes of the file (See figure above title "Common Encyrption Header"). Setting files and configuration files are stored in the following locations:
- %USERPROFILE%\AppData\Local\Cisco\Unifed Communications\Jabber\CSF
- %USERPROFILE%\AppData\Remote\Cisco\Unifed Communications\Jabber\CSF
- Program Files (x86)\Cisco Systems\Cisco Jabber
Log Files
Log files are located at %USERPROFILE%\AppData\Local\Cisco\Unifed Communications\Jabber\CSF: jabber, jabber.log.cef, jabber_ui. Generally, the log files contain debug information. The logs contain two pieces of information that can be useful to an investigator: CUCM and participant connection information and connection information. Since the Jabber (if phone services are active) would be configured on the CUCM, knowing the CUCM would provide investigators with the server to pull the user and device configuration. Also, IM&P resides in the same cluster and configured on the CUCM under System > Servers which may provide the instant messenger information such as contact lists. For participants, there is some information on status of other users; in testing, however, there was no direct reason why the SIP messages were logged within the log files.
Contact List and Persistent/Group Chat Rooms
IM&P stores contact lists for all users directly on the server which can be retrieved from the Administration Console under Bulk Administration > Contact List > Export Contact List. Contact lists provide an investigator a list of users associated with another user. The exported file contains the user id, user domain, contact id, contact domain, nickname, and group name. Nicknames and group names show how someone may feel about a person and give more insight into certain types of investigations. Persistent/Group chat rooms are created by administrators configured on the IM&P server; an investigator can find if they are enabled from Presence > Group Chat and Persistent Chat, but the chat rooms and messages are stored within a PostgreSQL external server from the IM&P server.
Further Research
This paper examined the Jabber Client for Windows only but there is a client for Android, iPad/iPhone, and Mac which might hold some interesting artifacts or possibility easier to acquire artifacts instead of from the Windows machines. Some of the information from the CUCM and IM&P servers was examined there are be more detailed information related to call logs, mobility, and other information which, similar to a large telephone company, will help investigators with call access logs. Other features are voice mail (Cisco Unity) and call recording (Cisco MediaSense, end-of-life as of 2020) or third-party solution) contain a plenty of information for investigators both generally through the administration console but, forensically, as servers, they can be changed without permission [12].
Conclusion
Cisco Jabber is a complete collaboration solution requiring a complex set of servers and configurations for use in an enterprise. However, being complex, Cisco Jabber’s end-user functionally remains easy for employee to utilize for their daily company business. The complexity does pose a problem during this paper for where information is stored and how to retrieve that information. As noted, Cisco Jabber client keeps most of its information stored locally in encrypted form; it does store contact lists, some chats, and some history on other servers which maybe retrieved and examined during an investigation. More research would need to be done to examine Cisco servers which are based on CentOS find different artifacts throughout the collaboration domain.
References
[1] https://marketrealist.com/2018/04/who-leads-the-collaboration-market-cisco-or-microsoft/
[2] https://www.britannica.com/topic/Cisco-Systems-Inc
[3] https://www.britannica.com/biography/John-T-Chambers
[4] https://newsroom.cisco.com/press-release-content?type=webcontent&articleId=4524095
[5] https://web.archive.org/web/20200928021835/https://www.solutel.com/new-features-of-cisco-jabber-with-jabber-12-5/?lang=en
[6] https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/jabber/12_5/Planning_Guide/cjab_b_planning-guide-for-cisco-jabber-125/cjab_b_planning-guide-for-cisco-jabber-125_chapter_010.html
[7] https://ericzimmerman.github.io/KapeDocs/#!index.md
[8] https://www.youtube.com/watch?v=YF-jDoh8BFM
[9] http://accessdata.com/about/who-we-are
[10] https://marketing.accessdata.com/ftkimager4.2.0
[11] https://www.vmware.com/support/developer/vddk/vmdk_50_technote.pdf
[12] https://community.cisco.com/t5/collaboration-voice-and-video/cisco-mediasense-end-of-life-faq/ta-p/3636105