UMLinux and Malware Analysis

While reading Forensic Discovery by Dan Famer and Wietse Venema, I ran across some thing called ReVirt for performing malware analysis. I pulled up the 2002 paper written by George W. Dunlap, Samuel T. King, Sukru Cina, Murtaza A. Basrai, and Peter M. Chen titled ReVirt: Enabling Intrustion Analysis through Virtual-Machine Logging and Replay.
In the paper, the authors exclaim that ReVirt solves two problems: improving the integrity of the logger being used and improving the completeness of the logger to capture data. The method of protecting the host computer is through the usage of UMLinux OS-on-OS structure. I have not seen this type of Linux before, so I took a examine of the SourceForge page (linked above).
In the basic sense, UMLinux provides a secure way to run Linux kernel and operating system on a Linux system in User-Mode. Linux provides two 'modes' to execute processes: kernel and user. Kernel being the most privileged mode normally reserved for kernel and system processes while user mode is the least privileged hosting all user-created processes. This separation provides a clear security boundary to protect a system. A more in-depth article is on Linux Journal: "Kernel Mode Linux".
Why is running UMLinux in user-mode important? The primary reason that even if a rogue process managed to escape the virtualization process, it would be contained within a normal user privilege level instead of full administration/root access. UMLinux project site provides instructions of running Linux kernel 2.6.x through a virtual machine on the command line. Note: No virtualization software needs to be installed.
ReVirt uses UMLinux as a loadable kernel in the below architecture diagram:
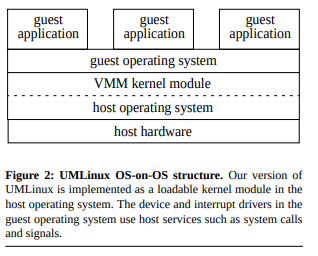
This produces a secure environment (at least according to the paper) to run and test untrusted applications. ReVirt also logs all actions performed by system calls within the VMM (virtual machine monitor) and it can actually rewind and replay any set of instructions. Providing this capability allows system administrators and malware analysts ability to closely examine the untrusted application.
ReVirt major abilities are really interesting, but how does that apply to current technology? One of the newish types of environment created for malware analysis is REMnux. You can learn REMnux in SANS Institute's Reverse-Engineering Malware training. REMnux provides a full suite of tools created to work on malware. ReVirt specifically deals with the virtualization of a system to work on untrusted application. In contrast, REMnux provides some virtualization technology (VMWare and Docker) but a ton of tools for analyst of application specifically malware.
Something to think about though. REMnux is suppose to be put on to an untrusted system in a untrusted network zone. Docker is coming to the space to run application within secure and clean environment. In the meantime, ReVirt and REMnux each provide a way to accomplish similar tasks and they are different; I wonder if REMnux could benefit from something from ReVirt. Joining these two together probably can even a new way to exam applications and malware analysis.